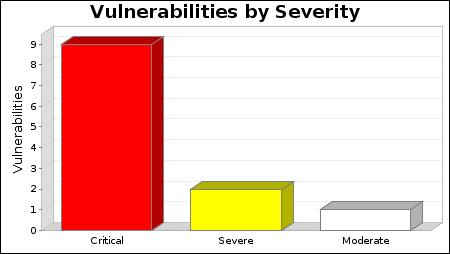
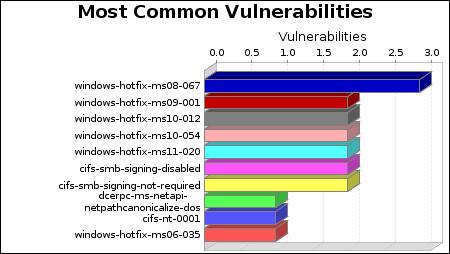
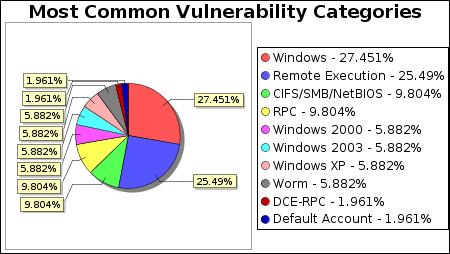
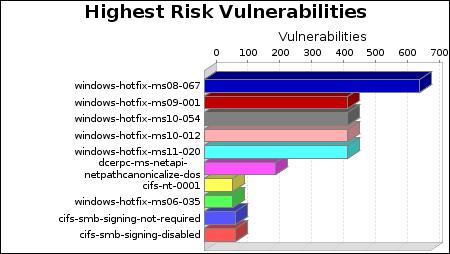
-
Microsoft Windows 2000 SP4 (x86), Microsoft Windows 2000 Professional
SP4 (x86), Microsoft Windows 2000 Server SP4 (x86), Microsoft Windows
2000 Advanced Server SP4 (x86), Microsoft Windows 2000 Datacenter Server
SP4 (x86)
Download and install Microsoft patch Windows2000-KB971468-x86-ENU.EXE (621304 bytes)
Download and apply the patch from:
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows2000-kb971468-x86-enu_d951943f14a5e6e52fbbbed11ae55882c685795c.exe (
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows2000-kb971468-x86-enu_d951943f14a5e6e52fbbbed11ae55882c685795c.exe
)
-
Microsoft Windows 7 < SP1 (x86_64), Microsoft Windows 7 Home,
Basic Edition < SP1 (x86_64), Microsoft Windows 7 Home, Basic N
Edition < SP1 (x86_64), Microsoft Windows 7 Home, Premium Edition
< SP1 (x86_64), Microsoft Windows 7 Home, Premium N Edition < SP1
(x86_64), Microsoft Windows 7 Ultimate Edition < SP1 (x86_64),
Microsoft Windows 7 Ultimate N Edition < SP1 (x86_64), Microsoft
Windows 7 Enterprise Edition < SP1 (x86_64), Microsoft Windows 7
Enterprise N Edition < SP1 (x86_64), Microsoft Windows 7 Professional
Edition < SP1 (x86_64), Microsoft Windows 7 Starter Edition < SP1
(x86_64), Microsoft Windows 7 Starter N Edition < SP1 (x86_64)
Download and install Microsoft patch Windows6.1-KB971468-x64.cab (312331 bytes)
Download and apply the patch from:
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows6.1-kb971468-x64_3a3cb2d4ce0f6bb55955bb8098a998b3f125ee49.cab (
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows6.1-kb971468-x64_3a3cb2d4ce0f6bb55955bb8098a998b3f125ee49.cab
)
-
Microsoft Windows Server 2008 SP2 OR SP1 (ia64), Microsoft Windows
Server 2008 Enterprise Edition SP2 OR SP1 (ia64), Microsoft Windows
Server 2008 Standard Edition SP2 OR SP1 (ia64), Microsoft Windows Server
2008 Datacenter Edition SP2 OR SP1 (ia64), Microsoft Windows Server
2008 HPC Edition SP2 OR SP1 (ia64), Microsoft Windows Server 2008 Web
Edition SP2 OR SP1 (ia64), Microsoft Windows Server 2008 Storage Edition
SP2 OR SP1 (ia64), Microsoft Windows Small Business Server 2008 SP2 OR
SP1 (ia64), Microsoft Windows Essential Business Server 2008 SP2 OR SP1
(ia64)
Download and install Microsoft patch Windows6.0-KB971468-ia64.cab (625509 bytes)
Download and apply the patch from:
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows6.0-kb971468-ia64_128eb8cad7194b012b81e9b1755bd35a3b46fab4.cab (
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows6.0-kb971468-ia64_128eb8cad7194b012b81e9b1755bd35a3b46fab4.cab
)
-
Microsoft Windows Server 2003 SP2 (x86_64), Microsoft Windows Server
2003, Standard Edition SP2 (x86_64), Microsoft Windows Server 2003,
Enterprise Edition SP2 (x86_64), Microsoft Windows Server 2003,
Datacenter Edition SP2 (x86_64), Microsoft Windows Server 2003, Web
Edition SP2 (x86_64), Microsoft Windows Small Business Server 2003 SP2
(x86_64)
Download and install Microsoft patch WindowsServer2003.WindowsXP-KB971468-x64-ENU.exe (1026944 bytes)
Download and apply the patch from:
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windowsserver2003.windowsxp-kb971468-x64-enu_8ea00e574a923da8a3aa9205a07780ed0a8741fa.exe (
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windowsserver2003.windowsxp-kb971468-x64-enu_8ea00e574a923da8a3aa9205a07780ed0a8741fa.exe
)
-
Microsoft Windows Server 2008 R2 < SP1 (ia64), Microsoft Windows
Server 2008 R2, Enterprise Edition < SP1 (ia64), Microsoft Windows
Server 2008 R2, Standard Edition < SP1 (ia64), Microsoft Windows
Server 2008 R2, Datacenter Edition < SP1 (ia64), Microsoft Windows
Server 2008 R2, Web Edition < SP1 (ia64)
Download and install Microsoft patch Windows6.1-KB971468-ia64.cab (580941 bytes)
Download and apply the patch from:
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows6.1-kb971468-ia64_414bf40b7690407c9ec9586ac8de40ff824e53a9.cab (
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows6.1-kb971468-ia64_414bf40b7690407c9ec9586ac8de40ff824e53a9.cab
)
-
Microsoft Windows Server 2008 R2 < SP1 (x86_64), Microsoft Windows
Server 2008 R2, Enterprise Edition < SP1 (x86_64), Microsoft Windows
Server 2008 R2, Standard Edition < SP1 (x86_64), Microsoft Windows
Server 2008 R2, Datacenter Edition < SP1 (x86_64), Microsoft Windows
Server 2008 R2, Web Edition < SP1 (x86_64)
Download and install Microsoft patch Windows6.1-KB971468-x64.cab (312331 bytes)
Download and apply the patch from:
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows6.1-kb971468-x64_3a3cb2d4ce0f6bb55955bb8098a998b3f125ee49.cab (
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows6.1-kb971468-x64_3a3cb2d4ce0f6bb55955bb8098a998b3f125ee49.cab
)
-
Microsoft Windows Server 2003 SP2 (x86), Microsoft Windows Server
2003, Standard Edition SP2 (x86), Microsoft Windows Server 2003,
Enterprise Edition SP2 (x86), Microsoft Windows Server 2003, Datacenter
Edition SP2 (x86), Microsoft Windows Server 2003, Web Edition SP2 (x86),
Microsoft Windows Small Business Server 2003 SP2 (x86)
Download and install Microsoft patch WindowsServer2003-KB971468-x86-ENU.exe (681856 bytes)
Download and apply the patch from:
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windowsserver2003-kb971468-x86-enu_b6dcb60d113c4affd98b5bae0dfd1f5a785ae64d.exe (
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windowsserver2003-kb971468-x86-enu_b6dcb60d113c4affd98b5bae0dfd1f5a785ae64d.exe
)
-
Microsoft Windows Server 2003 SP2 (ia64), Microsoft Windows Server
2003, Standard Edition SP2 (ia64), Microsoft Windows Server 2003,
Enterprise Edition SP2 (ia64), Microsoft Windows Server 2003, Datacenter
Edition SP2 (ia64), Microsoft Windows Server 2003, Web Edition SP2
(ia64), Microsoft Windows Small Business Server 2003 SP2 (ia64)
Download and install Microsoft patch WindowsServer2003-KB971468-ia64-ENU.exe (1589632 bytes)
Download and apply the patch from:
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windowsserver2003-kb971468-ia64-enu_faece6ff07ec2a029b74f49a959f1510eb38f3e7.exe (
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windowsserver2003-kb971468-ia64-enu_faece6ff07ec2a029b74f49a959f1510eb38f3e7.exe
)
-
Microsoft Windows 7 < SP1 (x86), Microsoft Windows 7 Home, Basic
Edition < SP1 (x86), Microsoft Windows 7 Home, Basic N Edition <
SP1 (x86), Microsoft Windows 7 Home, Premium Edition < SP1 (x86),
Microsoft Windows 7 Home, Premium N Edition < SP1 (x86), Microsoft
Windows 7 Ultimate Edition < SP1 (x86), Microsoft Windows 7 Ultimate N
Edition < SP1 (x86), Microsoft Windows 7 Enterprise Edition < SP1
(x86), Microsoft Windows 7 Enterprise N Edition < SP1 (x86),
Microsoft Windows 7 Professional Edition < SP1 (x86), Microsoft
Windows 7 Starter Edition < SP1 (x86), Microsoft Windows 7 Starter N
Edition < SP1 (x86)
Download and install Microsoft patch Windows6.1-KB971468-x86.cab (224255 bytes)
Download and apply the patch from:
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows6.1-kb971468-x86_79bba3989c41d43fce69d5d04709f061c3c6f5f5.cab (
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows6.1-kb971468-x86_79bba3989c41d43fce69d5d04709f061c3c6f5f5.cab
)
-
Microsoft Windows XP Professional SP3 OR SP2 (x86), Microsoft Windows XP Home SP3 OR SP2 (x86)
Download and install Microsoft patch WindowsXP-KB971468-x86-ENU.exe (664952 bytes)
Download and apply the patch from:
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windowsxp-kb971468-x86-enu_68d7899c8b8462219daf40f02c6fb9f362b1ee6b.exe (
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windowsxp-kb971468-x86-enu_68d7899c8b8462219daf40f02c6fb9f362b1ee6b.exe
)
-
Microsoft Windows Vista SP2 OR < SP1 OR SP1 (x86), Microsoft
Windows Vista Home, Basic Edition SP2 OR < SP1 OR SP1 (x86),
Microsoft Windows Vista Home, Basic N Edition SP2 OR < SP1 OR SP1
(x86), Microsoft Windows Vista Home, Premium Edition SP2 OR < SP1 OR
SP1 (x86), Microsoft Windows Vista Ultimate Edition SP2 OR < SP1 OR
SP1 (x86), Microsoft Windows Vista Enterprise Edition SP2 OR < SP1 OR
SP1 (x86), Microsoft Windows Vista Business Edition SP2 OR < SP1 OR
SP1 (x86), Microsoft Windows Vista Business N Edition SP2 OR < SP1 OR
SP1 (x86), Microsoft Windows Vista Starter Edition SP2 OR < SP1 OR
SP1 (x86)
Download and install Microsoft patch Windows6.0-KB971468-x86.cab (319207 bytes)
Download and apply the patch from:
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows6.0-kb971468-x86_673ca9ff1fae6a26038f2e8764d07033c451de06.cab (
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows6.0-kb971468-x86_673ca9ff1fae6a26038f2e8764d07033c451de06.cab
)
-
Microsoft Windows Server 2008 SP2 OR SP1 (x86_64), Microsoft Windows
Server 2008 Enterprise Edition SP2 OR SP1 (x86_64), Microsoft Windows
Server 2008 Standard Edition SP2 OR SP1 (x86_64), Microsoft Windows
Server 2008 Datacenter Edition SP2 OR SP1 (x86_64), Microsoft Windows
Server 2008 HPC Edition SP2 OR SP1 (x86_64), Microsoft Windows Server
2008 Web Edition SP2 OR SP1 (x86_64), Microsoft Windows Server 2008
Storage Edition SP2 OR SP1 (x86_64), Microsoft Windows Small Business
Server 2008 SP2 OR SP1 (x86_64), Microsoft Windows Essential Business
Server 2008 SP2 OR SP1 (x86_64)
Download and install Microsoft patch Windows6.0-KB971468-x64.cab (595103 bytes)
Download and apply the patch from:
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows6.0-kb971468-x64_b33a54f7e4f6f3f8664b5f240ab148f770a28660.cab (
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows6.0-kb971468-x64_b33a54f7e4f6f3f8664b5f240ab148f770a28660.cab
)
-
Microsoft Windows XP Professional SP2 (x86_64)
Download and install Microsoft patch WindowsServer2003.WindowsXP-KB971468-x64-ENU.exe (1026944 bytes)
Download and apply the patch from:
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windowsserver2003.windowsxp-kb971468-x64-enu_8ea00e574a923da8a3aa9205a07780ed0a8741fa.exe (
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windowsserver2003.windowsxp-kb971468-x64-enu_8ea00e574a923da8a3aa9205a07780ed0a8741fa.exe
)
-
Microsoft Windows Server 2008 SP2 OR SP1 (x86), Microsoft Windows
Server 2008 Enterprise Edition SP2 OR SP1 (x86), Microsoft Windows
Server 2008 Standard Edition SP2 OR SP1 (x86), Microsoft Windows Server
2008 Datacenter Edition SP2 OR SP1 (x86), Microsoft Windows Server 2008
HPC Edition SP2 OR SP1 (x86), Microsoft Windows Server 2008 Web Edition
SP2 OR SP1 (x86), Microsoft Windows Server 2008 Storage Edition SP2 OR
SP1 (x86), Microsoft Windows Small Business Server 2008 SP2 OR SP1
(x86), Microsoft Windows Essential Business Server 2008 SP2 OR SP1 (x86)
Download and install Microsoft patch Windows6.0-KB971468-x86.cab (319207 bytes)
Download and apply the patch from:
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows6.0-kb971468-x86_673ca9ff1fae6a26038f2e8764d07033c451de06.cab (
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows6.0-kb971468-x86_673ca9ff1fae6a26038f2e8764d07033c451de06.cab
)
-
Microsoft Windows Vista SP2 OR < SP1 OR SP1 (x86_64), Microsoft
Windows Vista Home, Basic Edition SP2 OR < SP1 OR SP1 (x86_64),
Microsoft Windows Vista Home, Basic N Edition SP2 OR < SP1 OR SP1
(x86_64), Microsoft Windows Vista Home, Premium Edition SP2 OR < SP1
OR SP1 (x86_64), Microsoft Windows Vista Ultimate Edition SP2 OR <
SP1 OR SP1 (x86_64), Microsoft Windows Vista Enterprise Edition SP2 OR
< SP1 OR SP1 (x86_64), Microsoft Windows Vista Business Edition SP2
OR < SP1 OR SP1 (x86_64), Microsoft Windows Vista Business N Edition
SP2 OR < SP1 OR SP1 (x86_64), Microsoft Windows Vista Starter Edition
SP2 OR < SP1 OR SP1 (x86_64)
Download and install Microsoft patch Windows6.0-KB971468-x64.cab (595103 bytes)
Download and apply the patch from:
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows6.0-kb971468-x64_b33a54f7e4f6f3f8664b5f240ab148f770a28660.cab (
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows6.0-kb971468-x64_b33a54f7e4f6f3f8664b5f240ab148f770a28660.cab
)
-
Microsoft Windows 2000 SP4 (x86), Microsoft Windows 2000 Professional
SP4 (x86), Microsoft Windows 2000 Server SP4 (x86), Microsoft Windows
2000 Advanced Server SP4 (x86), Microsoft Windows 2000 Datacenter Server
SP4 (x86)
Download and install Microsoft patch Windows2000-KB971468-x86-ENU.EXE (621304 bytes)
Download and apply the patch from:
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows2000-kb971468-x86-enu_d951943f14a5e6e52fbbbed11ae55882c685795c.exe (
http://download.windowsupdate.com/msdownload/update/software/secu/2010/01/windows2000-kb971468-x86-enu_d951943f14a5e6e52fbbbed11ae55882c685795c.exe
)